Многие бесплатные или условно-бесплатные программы перестают отображать рекламу после их регистрации или приобретения. Однако в некоторых программах используются сторонние Adware-утилиты. Иногда такие утилиты остаются установленными на компьютере пользователя и после регистрации или приобретения программы. В некоторых случаях удаление Adware-компонента может привести к нарушению функционирования программы.
Adware — это программы, которые предназначены для показа рекламы на вашем компьютере, перенаправления запросов поиска на рекламные веб-сайты и сбора маркетинговой информации о вас (например, какого рода сайты вы посещаете), чтобы реклама соответствовала вашим интересам.
Adware-программы, которые собирают данные с вашего согласия, не следует путать с троянскими программами-шпионами, которые собирают информацию без вашего разрешения и ведома. Если Adware-программа не уведомляет о сборе информации, она считается вредоносной, например, вредоносная программа троянец-шпион (Trojan-Spy).
Popular dating apps used worldwide, such as Tinder and Badoo, often become bait used to spread mobile malware or retrieve personal data to later bombard the users with unwanted ads or even spend their money on expensive paid subscriptions”, — explained Kaspersky Lab specialists.

According to Kaspersky Lab report, almost one in five users use online dating apps (19%). Of course, attackers do not miss the opportunity to monetize this interest. Banking Trojans use the popular Tinder and Badoo brands.
The company’s researchers found that mobile networks often use the names of popular dating services.
A total of 1963 malicious files were detected for mobile devices. In 1262 of them the name Tinder was used, and in 263 – Badoo.
Popular dating apps used worldwide, such as Tinder and Badoo, often become bait used to spread mobile malware or retrieve personal data to later bombard the users with unwanted ads or even spend their money on expensive paid subscriptions”, — explained Kaspersky Lab specialists.
So, one of the applications, which at first glance looks like Tinder, is actually a banking trojan that constantly requires the user to provide extended rights to the Google Accessibility Service, a service designed to facilitate the use of applications by people with disabilities. After obtaining these rights, the malware independently issues all the permissions necessary to steal money.
Another application after installation is fixed in a system called Settings, at startup it displays a fake error message and hides from the list of applications in order to return after some time to display intrusive advertising.
Тop 10 detections by the number of attacked users (by Kaspersky):
- HEUR:Trojan.AndroidOS.Hiddapp.ch
- HEUR:Trojan.AndroidOS.Boogr.gsh
- UDS:DangerousObject.Multi.Generic
- not-a-virus:HEUR:AdWare.AndroidOS.MobiDash.z
- not-a-virus:HEUR:AdWare.AndroidOS.Mobidash.ai
- not-a-virus:HEUR:RiskTool.AndroidOS.Frime.a
- HEUR:Trojan-SMS.AndroidOS.Opfake.a
- not-a-virus:HEUR:RiskTool.AndroidOS.Dnotua.ixj
- not-a-virus:HEUR:AdWare.AndroidOS.Mobidash.ag
- UDS:DangerousObject.AndroidOS.GenericML
In addition, scammers are developing phishing schemes that allow earning on the desire to find a partner for a date.
As part of one of the common tactics, a user gets to know a girl, and when it comes to making an appointment, she offers to go to the cinema, chooses a movie theater and a show herself and sends a link by which to book tickets. If a user pays for tickets, his money goes to scammers, and the person with whom he corresponded ceases to get in touch”, – said IS researchers.
In addition to phishing schemes, new fake copies of dating services regularly appear. scammers mostly use them to collect personal data.
Dating sites are very popular, and attackers do not miss the opportunity to play on it. We remind you to be careful and recommend downloading only legitimate versions of such services from application stores, and not sharing too much information about yourself with strangers,” – commented Kaspersky Lab experts.
Dating app users can avoid falling prey to cybercriminals by following these tips:
- Don’t install applications from untrusted sources, even if they are always advertised.
- Block the installation of programs from unknown sources.
- Check the reputation and user feedback of the dating website one is planning to visit.
- Use reliable security solutions that offer advanced protection on PCs and mobile devices.
But this does not mean that you should be sad on Valentine’s Day and not trust anyone. Kaspersky Lab, for example, had enough of its problems too.
Xchanging, an insurance managed service provider, was hit with a ransomware attack over the weekend, parent company DXC Technology reports. The company revealed few details except that customer data wasn’t compromised.
Xchanging, an insurance managed service provider, was hit with a ransomware attack over the weekend, parent company DXC Technology reports. The company revealed few details except that customer data wasn’t compromised.
Cybercriminals are using mobile devices more than PCs to deliver attacks via adult content that hides malware, Kaspersky has found. The most common tactics involve software that redirects users to unwanted content or advertising, with one app, AdWare.AndroidOS.Agent.f, used in 35.18% of adult-content-related attacks on mobile users.
Cybercriminals are exploiting public concern about the coronavirus outbreak by circulating files that purport to include information about illness prevention and detection but that actually contain malware, Kaspersky Lab says. Researchers have found such files formatted as PDFs, DOCs and MP4s with names including the following:
- Worm.VBS.Dinihou.r
- Worm.Python.Agent.c
- UDS:DangerousObject.Multi.Generic
- Trojan.WinLNK.Agent.ew
- HEUR:Trojan.WinLNK.Agent.gen
- HEUR:Trojan.PDF.Badur.b
What should you do if your antivirus detects something it calls “not-a-virus”? What kind of applications are behind this message, and what is all the fuss about?
What is adware?
Adware is software with advertising material. This type of software can show you advertisements, alter search results, collect user data to show targeted contextual advertising, or all of the above.
Adware technically is not malicious, but there is nothing good about it, either. All hell may break loose when a few dozen adware applications sneak onto a computer and start to compete with one another for resources.
That said, adware is legitimate software that is installed on computers with the formal consent of users — the catch is, users may not notice a preselected check box during the installation of another application, and thus agree to install adware. Other instances of such monkey business abound, but they are all alike in one way: If users read everything carefully, then they can decline the adware installation.
If adware does not notify the user of its attempt to install itself on the computer, then Kaspersky Internet Security treats it as a malicious Trojan. In that case, the notification will have a red frame, not a yellow one, and the application will be blocked immediately. By the way, you can check out this article in which we discuss what the frame colors of notification windows mean in our products.
What is riskware?
Riskware is a slightly different matter. Applications of this type were initially created as useful tools, and they may be used on a computer for their stated purposes. But quite often, malefactors install riskware — certainly without the user’s knowledge — to pursue their own goals. You can check out the full list of application types that we consider riskware here.
For example, remote computer management software (remote admin) is considered riskware. If you installed one of these applications yourself — and you know what you are doing — then there’s no harm in having it. However, this type of application is frequently included as part of a malware package; in that case, users need to know about it.
Another example is download managers. Many of them do make it easy and convenient to download files, but some of them appear to operate on the brink of breaking the rules, for example, attempting to download extra files while showing a notification using a gray font on a gray background.
Another popular type of riskware is browser toolbars, which may also be adware, depending on their supported features and persistence. And some browser extensions may be considered riskware.
Also, miners fall into the riskware category. Miners are applications for mining bitcoins. Needless to say, if it was you who chose to install a miner on your computer, then everything should be all right. But if someone else did it without your consent, then the installed software is consuming your computer’s resources for their gain.
By default, Kaspersky Internet Security does not show notifications of riskware detection. Now, if you go into the “Threats and Exclusions” section of the settings and check the “Detect other software…” option, then Kaspersky Internet Security will inform you about riskware as well.
Still, it will only inform you. The antivirus does not block or delete riskware by default so as not to hinder the legitimate use of these applications. You will not, in fact, see the word “riskware” anywhere in notifications. Only specific information will be shown, telling you if an application is for remote administration, if it is a downloader, or something else.
As soon as riskware starts to download any malware components, it will be reclassified as a Trojan and blocked regardless of whether the “Detect other software…” option is checked.
Adware or riskware has been detected. What is the next step?
Kaspersky Internet Security shows detection notifications for such applications so that you know that they are installed on your computer. It is possible that you installed them on purpose: As we said, riskware may be very useful. In that case, there is no reason to worry.
It is also possible that another “not-a-virus” has crawled into your computer without your noticing it. In that case, you need to know if the application is related to either riskware or adware. That is why users are given the chance to choose what to do with the application. If you did not install it, you should probably delete it.
Once again, there are adware programs that change your start page, your search engine, or even fiddle with the shortcuts on your computer that open your browsers. There is also, of course, different adware for different devices and operating systems. So you might have to cope with mobile/Android adware, Mac adware, or Windows adware.
Mac adware
For the most part, adware for Macs rides inside a Trojan, malware that takes its name from the Trojan horse of Greek mythology. The Trojan portrays itself as something you want. Maybe a player, or some kind of plug-in. It might even be skulking around inside a legitimate software download from a disreputable site. Either way, it promises you one thing, but delivers adware in a bait-and-switch.
As far as the signs of a Mac adware infection go, they mirror the symptoms you see on Windows systems. Ads pop up where they shouldn’t be—literally everywhere. Something changes your homepage without so much as a how do you do. Familiar web pages just don’t look right anymore, and when you click on a link, you find yourself redirected to an entirely different site. It might even substitute a new search engine for your regular one.
So in the end, Macs, while less vulnerable than Windows computers, can still have a security problem with adware. More on what to do about it below.
Keep your Android phone safe from hackers with regular software updates.
How malware on your phone works
Mobile malware typically takes one of two approaches, said Adam Bauer, a security researcher for mobile security company Lookout. The first type of malware tricks you into granting permissions that let it access sensitive information.
Keep your Android phone safe from hackers with regular software updates.
That’s where the Ads Blocker app fits in, and many of the permissions it requested sound like something a real ad blocker would have needed. But they also let the app run constantly in the background and show users ads even when they were using unrelated apps.
The second type of malware exploits vulnerabilities in phones, gaining access to sensitive information by giving itself administrator privileges. That reduces the need to get users to click «OK» on permissions requests, making it easier for malware to run without users noticing its presence on the device.
Code for displaying ads when the screen is unlocked
Recently, we’ve been noticing ever more dubious advertising libraries in popular apps on Google Play. The monetization methods used in such SDKs can pose a threat to users, yet they pull in more revenue for developers than whitelisted ad modules due to the greater number of views. In this post we will look into a few examples of suspicious-looking ad modules that we discovered in popular apps earlier this year.
One of the applications we researched was a popular app that allows users to ask questions anonymously. Integrated into the code of an earlier version of the app was the module com.haskfm.h5mob. Its task was to show intrusive advertising (in breach of the Google Play rules) when the user unlocked the phone.
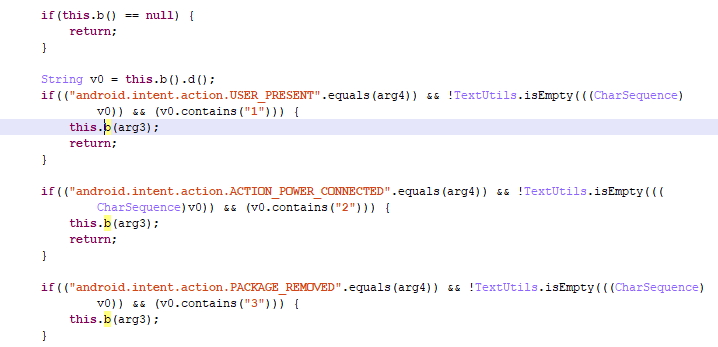
Code for displaying ads when the screen is unlocked
In other words, the module can show ads whether the app is running or not. The ad can simply pop up on the main screen all on its own, causing a nuisance for the user. We passed our findings to the app developers, who promptly removed com.haskfm.h5mob. However, this module remains interesting from technical point of view.
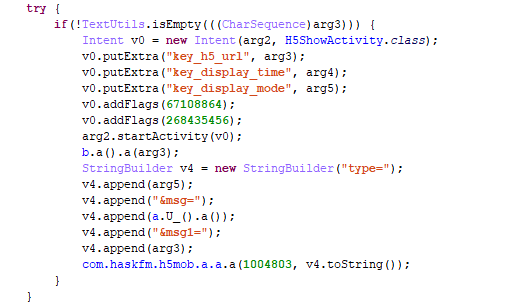
In this application to receive advertising offers, the module connects to the C&C servers, whose addresses are encrypted in the app code.
Decrypting the C&C addresses
The C&C response contains the display parameters and the platforms used to receive ads.
Earlier we detected a similar ad module in apps without a payload. For example, the code in the app com.android.ggtoolkit_tw_xd, which we detect as not-a-virus:AdWare.AndroidOS.Magic.a, contains the same features and is managed from the same C&C as the com.haskfm.h5mob module. However, this adware app has no graphical interface to speak of, is not displayed in the device’s app menu, and serves only to display intrusive ads as described above. It looks something like this: adware_in-app_video.mp4
While, as previously mentioned, the creators of the application described in the first example, promptly removed the ad module, not all Android developers are so conscientious. For example, the Cut – CutOut & Photo Background Editor app does not hesitate to treat users to a half-screen ad as soon as the smartphone is unlocked, regardless of whether the app is running or not.
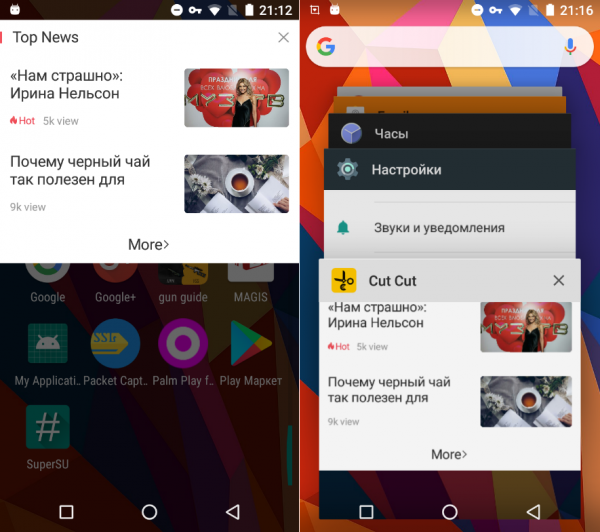
Likewise the Fast Cleaner — SpeedBooster & Cleaner app.
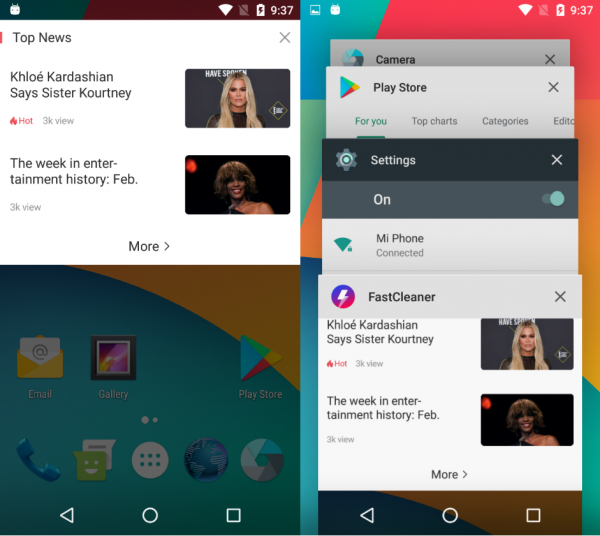
In both apps, the library com.vision.lib handles the display of advertising.
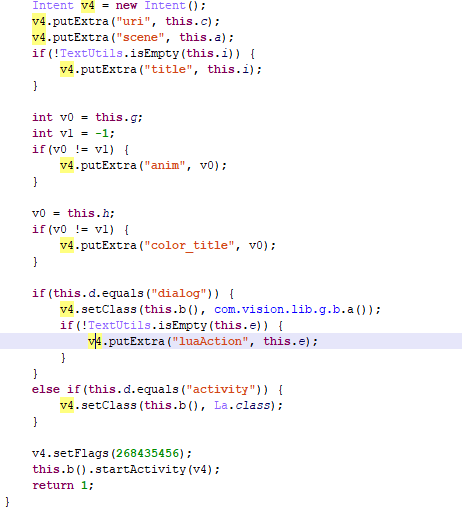
Display of advertising
At the time of writing this article, the developers of both apps had not responded to our requests.
Cодержание

